Accelerating Global Business through ATM Security Practices
1.Introduction
Automated teller machines (ATMs) are common around the world and have become an important part of people's everyday lives. ATMs provide financial services such as fund withdrawal and deposit for cardholders. Over three million ATMs were available worldwide in 2015. However, they also attract criminals seeking illegal profits and thus ATM security is extremely important.
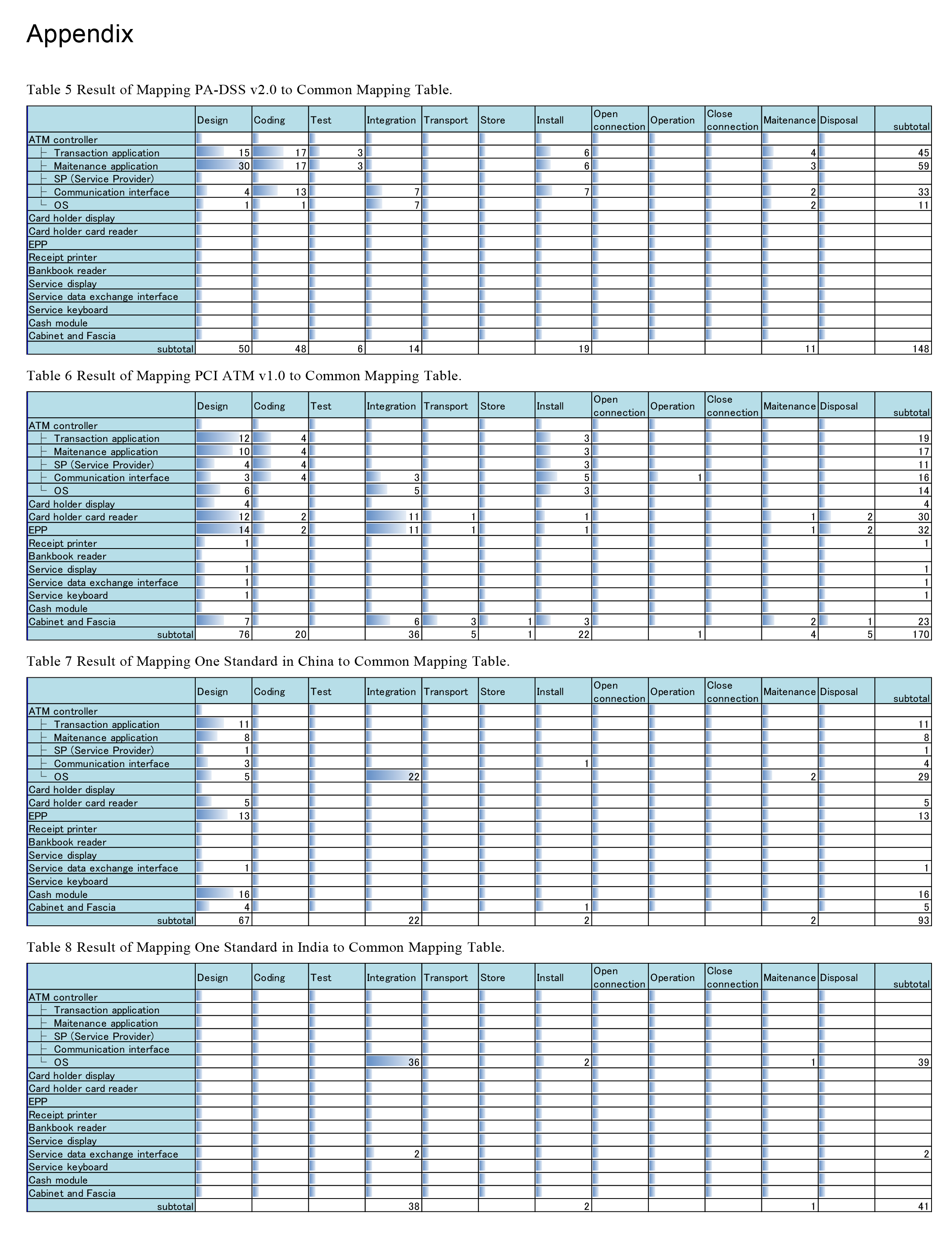
We classify different aspects of ATM security into four areas, as shown in Figure 1.
- End user security covers topics such as user education and user feedback.
- System security covers topics such as network security and security monitoring.
- Product security covers topics such as anti-virus software and data encryption.
- Component security covers topics such as tamper resistance.
When developing an online system, mainly the bank determines whether to use bank-owned or rented-out ATMs and what the ATM security specifications should be. For example, the bank decides whether to use magnetic stripe cards or integrated circuit cards. ATM vendors are then required to configure the security functions of the ATMs to match the bank's decisions.
However, having a vast number of security functions would increase the costs of ATMs. Therefore, it is important to strike a balance between function and cost.
This paper focuses on ATMs as products and an ATM vendor that is improving security capabilities while expanding into the global market.
2. Outline of ATM Product Security
In academia, many studies treat ATM security as system security because ATMs come across as black boxes that are difficult to investigate. ATMs should instead be viewed as complete products in and of themselves. However, only a few studies have examined ATM product security.
In industry, ATM Marketplace [1] is a well-known source of information on ATM product security. The Information-technology Promotion Agency (IPA) of Japan analyzed ATM product security as an embedded system [2]. In addition, The Connected Consumer Device Security Council (CCDS) has examined ATM product security [3].
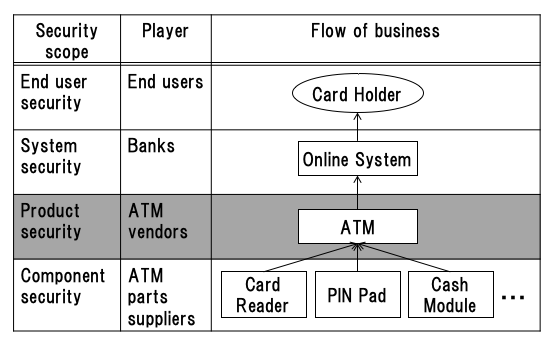
ATM vendors hold several patents related to ATM product security. The specifications of the patents include keywords such as those shown in Table 1. Keyword trends are similar among different ATM vendors. The top keywords are "banknote" and "transaction," and the next most frequent keywords are "card" and "cash module." These keywords refer to assets that must be protected. The threats to ATMs, however, vary as attack technologies advance and therefore security countermeasures such as "camera" and "IA&A" are frequent keywords.
(IA&A: Identification, Authentication, and Authorization. Feedback refers to the image and sound notifications received by a cardholder. PIN: Personal Identification Number.)
3. ATM Business and Security Challenges
3.1 Domestic Business
Hitachi-Omron Terminal Solutions Corporation [4] was established by merging the financial automatic machine divisions of Hitachi and of Omron in 2004. This vendor has occupied the top market share in the domestic ATM market, and its ATMs are used in many banks and convenience stores in Japan.
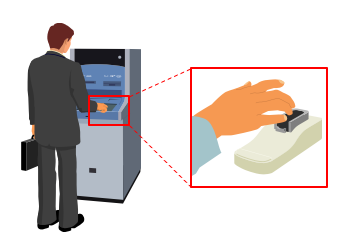
Its ATMs are characterized by an equipped finger-vein authentication system [5] for personal identification, illustrated in Figure 2. In a report by ATM software company KAL [6], it was stated that this finger-vein recognition system has been widely adopted throughout Japan.
3.2 Global Business
As Figure 3 highlights, the ATM business of Hitachi-Omron is active not only in Japan, but also in global markets such as China and India. The ATM markets in China and India are growing.
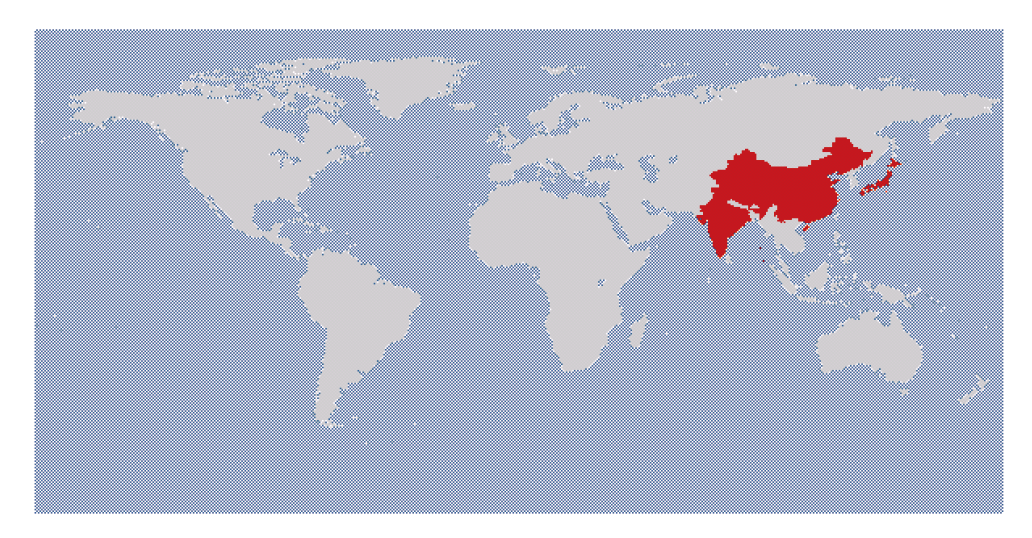
3.3 Security Challenges
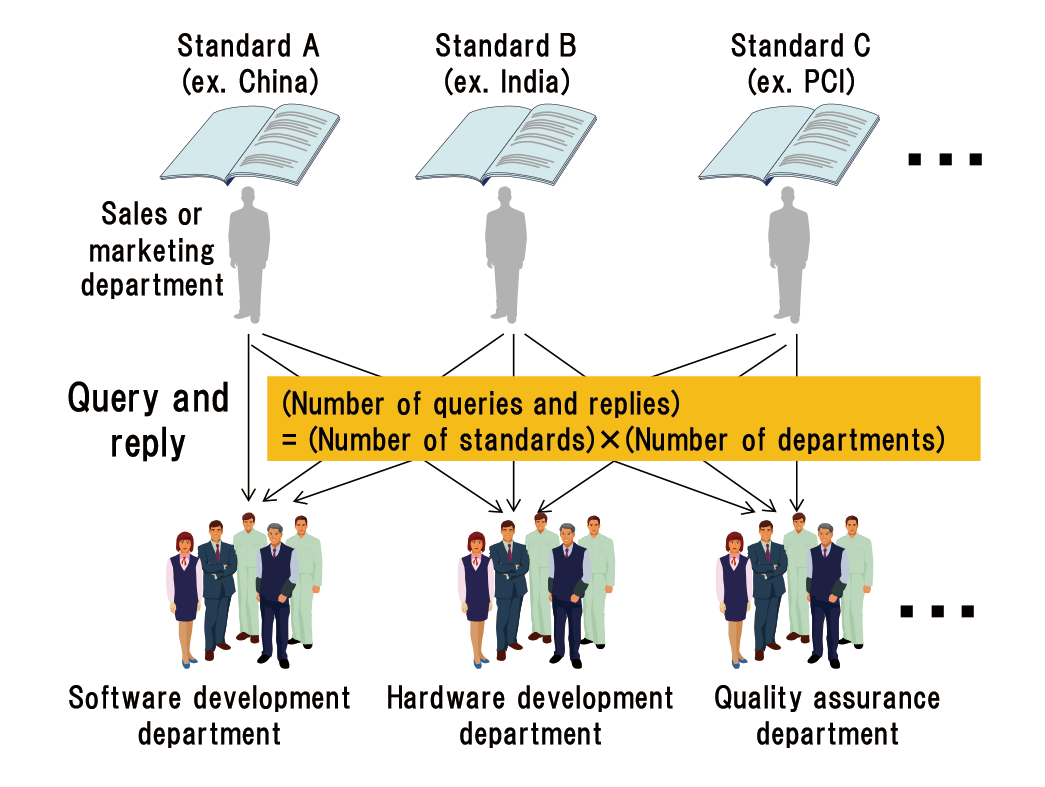
An expansion from the domestic market to global markets requires ATM vendors to be aware of new aspects of security. More often, security breaches occur globally than domestically. Consequently, for businesses that want to join the global market, security functions become major barriers. In addition, each country has its own regulations, which are different from those of other countries, and these regulations may be updated frequently. Conforming to the regulations is necessary for efficiency and promptness.
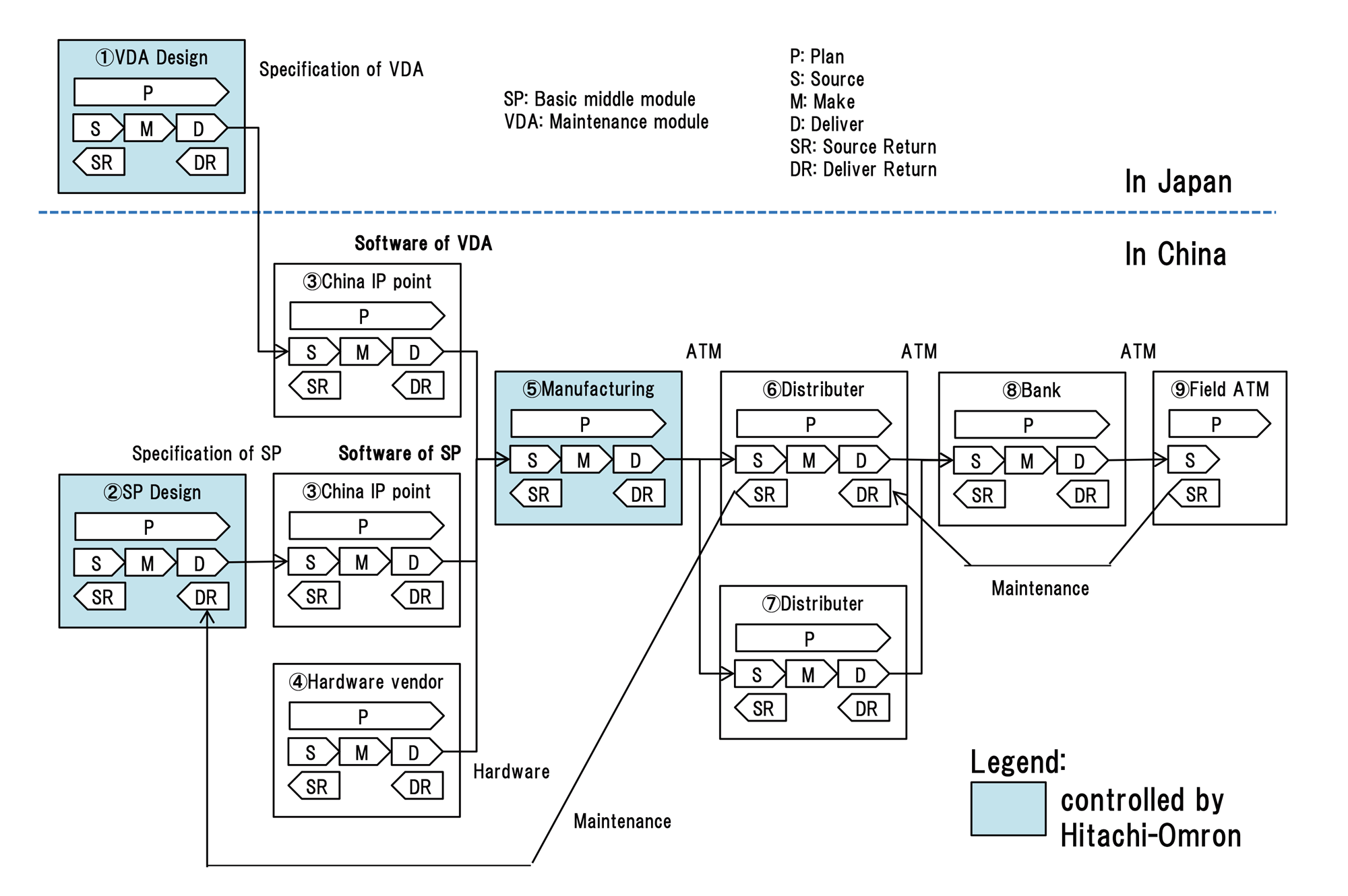
Challenge 1: The quality of ATM security should be maintained throughout the ATM supply chain.The supply chain of ATMs can easily change when expanding from a domestic to a global market. For example, when ATMs are designed in Japan but arranged to be sold to foreign countries, they will be manufactured in the other country where the goal is to cut down on expensive shipment costs. Consequently, even if ATMs have secure designs, the resulting ATM products may not be manufactured in a way that adequately matches that design. Therefore, sometimes, the quality of ATMs is affected by the supply chain, and ATM vendors cannot ignore the issue of maintaining quality.
The supply chain can be analyzed based on the supply chain operations reference (SCOR) model [7]. As Figure 4 shows, the SCOR model is composed of the following processes: "plan," "source," "make," "deliver," and "return." This model is useful because security both in and out of the vendor's control in the supply chain is identified through analysis to maintain product security.
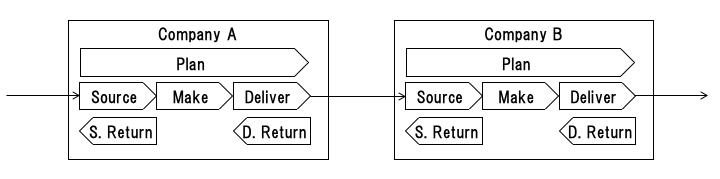
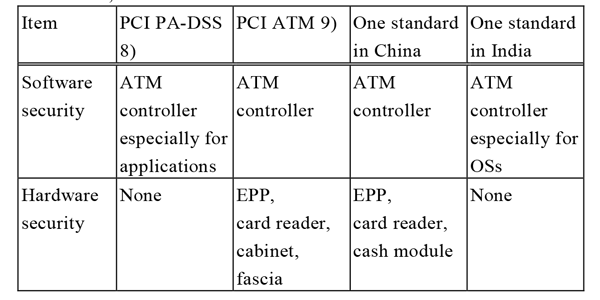
An ATM vendor that expands its target market to another country will face the problem of new regulations and/or standards in the target country. As Table 2 shows, vendors must conform to many regulations.
(PCI: Payment Card Industry, EPP: Encrypting PIN Pad, fascia: ATM front, available for user cardholder interaction)
These regulations and standards are updated every few years. As Figure 5 shows, the greater the number of new or updated regulations or standards, the higher the cost of internal processes such as query and reply become. Efficient ways to reduce internal costs should be considered.
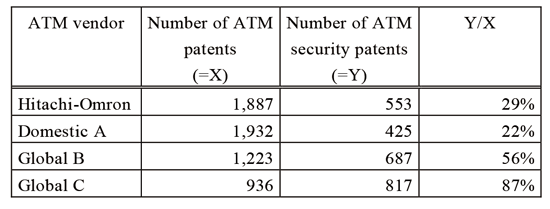
As Table 3 shows, while global vendors own fewer ATM patents (X value in Table 3) than domestic vendors do, including Hitachi-Omron, the ratio of security patents to total patents (Y/X value in Table 3) for global vendors is higher than that for domestic vendors. This shows that, in global markets, security features and security capabilities are more important than other functions and features. Therefore, much more than before, it is important to enhance security functions and capabilities to expand its own business worldwide.
4. Security Controls and Practices
We have improved Hitachi-Omron's ATM security to reach a level equal to the global standard, with the goal of becoming the world’s competitive vendor in secure ATMs. The following sections describe security practices and controls in the last decade.
- Setting a Security Target for ATMs (section 4.1)
- Conforming to regulations and standards (section 4.2)
- Enhancing supply chain security (section 4.3)
- Summarizing specifications for ATM security (section 4.4)
4.1 First Step: Setting a Security Target for ATMs
ISO/IEC 15408 (Common Criteria) [10] is a well-known international standard for evaluating IT security, and evaluation based on this standard is performed in over 20 countries. The evaluation system is rigid. Two Protection Profiles related to ATM security [11] [12] have been made public. The process for developing a Security Target (ST) is as follows:
- identifies the Target of Evaluation (TOE);
- identifies assets to be protected;
- determines all threats to confidentiality, integrity, and availability of the assets;
- evaluates the risk of each threat;
- establishes security objectives; and
- maps the security objectives to requirements for security functions.
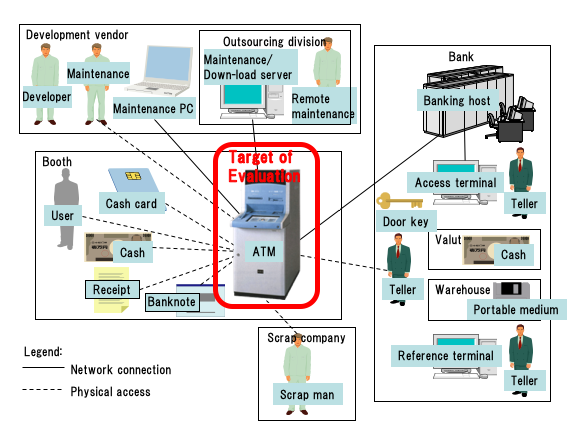
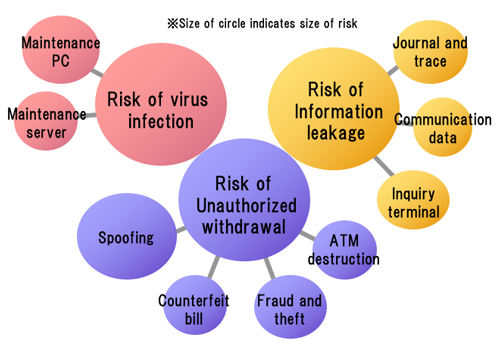
We developed Hitachi-Omron's non-public ATM ST, the TOE of which is shown in Figure 6; Figure 7 shows the risk evaluation results. According to the ST, we recognized security risks posed to ATMs; their security countermeasures are discussed in the next section.
- Risk of unauthorized withdrawal.
- Risk of virus infection.
- Risk of information leakage.
4.2 Second Step: Conforming to Regulations and Standards
To conform to many regulations and standards efficiently and promptly, it is important to identify which requirements are similar and which are unique. A common mapping table is useful to coordinate regulations. As Figure 8 shows, the mapping table is composed of a two-dimensional matrix that has a where-axis and a when-axis. Requirements are arranged in two steps.
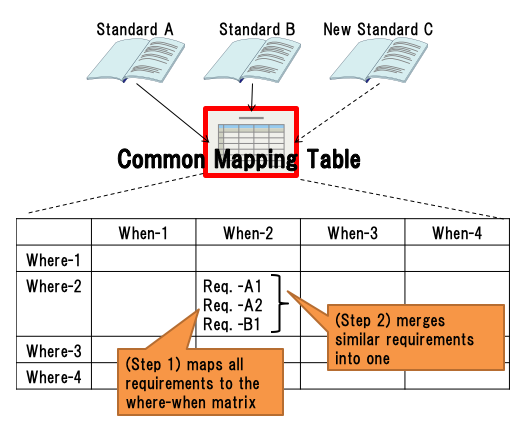
- Step 1: All the requirements are mapped into the where-when matrix.
- Step 2: In each cell, similar requirements are merged into one new requirement.
We used the common mapping table by setting the where-axis as 16 ATM components and the when-axis as 12 ATM development and operation lifecycles; the results of mapping all the requirements are shown in the Appendix in Table 5-8. In the mapping process, the design-axis in Table 5-8 is apparently essential; moreover, the following two items are also essential and common.
- OS hardening (the integration-axis in Table 5-8)
ATMs use commercial OSs, and the OSs have many security configuration items. For defense-in-depth, OS hardening is critical. Hardening guidelines are available in the National Checklist Program [13]. Windows OS's security configurations can be checked using an automated tool such as the Security Compliance Manager [14]. - Secure coding (the coding-axis in Table 5-8)
In the process of producing source code, vulnerabilities such as buffer overflow and format string can easily slip into the source code. One set of well-known secure coding rules is the CERT coding standard [15], and plug-ins for development tools such as Visual Studio can be used to check some rules.
4.3 Third Step: Enhancing Supply Chain Security
As Figure 9 shows, global supply chains such as the Chinese or Indian markets can be represented using the SCOR model. Compared with the domestic market, the entities that can be controlled by the vendor are quite limited.
Moreover, the order of the priorities of quality, cost, and delivery is different from that of the domestic one. The attitude toward quality is quite different between the domestic and global markets because rapid modification of product flaws resulting from rapid program release is much more acceptable in global markets.
- Domestic market
Priority order is Quality, Cost, and Delivery. - Global market
Priority order is Delivery, Cost, and Quality.
Security is one aspect of quality. When performing rapid modifications of an ATM program, it is important to establish shared responsibility, which means sharing the risk between stakeholders—in other words, sharing the responsibility of implementing countermeasures between them.
To analyze shared responsibility, we applied a risk management framework according to ISO 31000 [16]. Specifically, a top event that is shared between one stakeholder and another is broken into basic events by the Fault Tree Analysis, and each basic event is assigned as the responsibility of one stakeholder. From a vendor's point of view, hardware security is very important as a point of trust in the context of the supply chain.
4.4 Summary of Specifications for ATM Security
By performing the steps in sections 4.1-3, we recognized the necessity and sufficiency of having security countermeasures and conducting the measures before serious security breaches occur. Hitachi-Omron makes itself ready to provide the following ATM-security professional products and services.
(1) Software Security- PCI PA-DSS-validated ATM controller [17]
- Application whitelisting
- OS hardening
- Secure coding
- Patching
- EPP certified by PCI [18]
- Card reader with anti-skimming technology
- Finger-vein recognizing UBReader certified by Common Criteria [19]
- Cash recycling module
- Cabinet
- Journal management service using cloud software
- ATM-security verification services (whitelisting, hardening, fuzzing, patching)
5. Toward a Security Eco-System
Maintaining security is a never-ending task, and it cannot be achieved by one ATM vendor alone. It is important to establish a security "eco-system" for sharing security-related intelligence. From our past decade of security experience, we have concluded that the eco-system is composed of the (1)-(4) players shown in Figure 10.
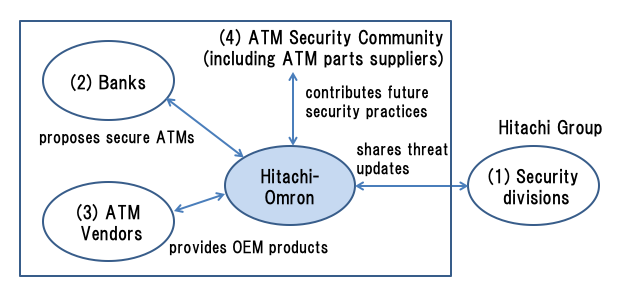
The Hitachi group maintains information securely by respecting all global regulations, and the R&D division [20] continues to develop new security technologies for this purpose. In particular, the security professionals of the Hitachi Incident Response Team [21] continue to improve prevention, detection, and recovery technology every day. We share and discuss security information with them to keep their knowledge and practices up to date.
(2) Cooperating with BanksHitachi-Omron is capable of designing secure ATMs together with banks. Its secure designs include a strong authentication system that uses a finger-vein biometrics device [5]. The know-how enbles to advise banks on how to improve ATM security.
(3) Cooperating with ATM VendorsAs an original equipment manufacturer, Hitachi-Omron provides cash recycling modules to other ATM vendors. The cash recycling mechanism can detect counterfeit banknotes so that ATM users never withdraw or deposit counterfeits.
(4) Cooperating with the Security CommunityHitachi-Omron is a member of security communities such as the ATM Industrial Association (ATMIA) [22], PCI [23], and CCDS [24]. This cooperation contributes to future business in both the short- and long-term.
Reasonable security cannot be achieved if one player is missing. If there is successful cooperation in the area of security, there will be more business.
6. Lessons for Generalization
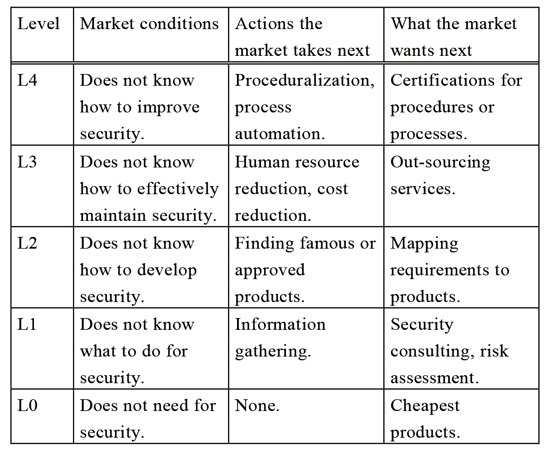
On the basis of the experience of expanding from a domestic to a global business, we feel that markets are capable of different levels of security in each country; Table 4 shows these levels. Security functions are necessary; however, what is more important is to identify what the market desires for future products. Acting in accordance with a market's level will guide to achieve successful security developments for the next market.
7. Summary
This paper explained the ATM security practices expanding its domestic business to the global. Many visitors from other countries will come to Japan when the 2020 Olympic Games are held in Tokyo. This means criminals may target financial systems, including ATMs, in Japan with various global techniques. Hitachi-Omron has been well trained through its global business and has improved its security capabilities. It is aiming to become the vendor with the highest level of ATM security in the world and supports secure and safe life through secure ATMs.
TrademarksVisual Studio is registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries.
References
- 1)ATM Marketplace, http://www.atmmarketplace.com/ (accessed 2017-10).
- 2)IPA: Research for Security Technical Map about Threats and Countermeasures of Embedded System, http://www.ipa.go.jp/security/fy18/reports/embedded/ (accessed 2017-10, in Japanese).
- 3)CCDS: Security Countermeasure Practice Guide for ATM Ver1.0, https://www.ccds.or.jp/public_document/ (accessed 2017-10, in Japanese).
- 4)Hitachi-Omron Terminal Solutions, Corp., http://www.hitachi-omron-ts.co.jp/ (accessed 2017-10).
- 5)Hitachi-Omron Terminal Solutions, Corp., Finger Vein Reader, http://www.hitachi.co.jp/products/it/veinid/global/products/embedded_devices_r.html (accessed 2018-6).
- 6)KAL: 2010 ATM Software Trends and Analysis (2010).
- 7)APICS: SCOR Framework, http://www.apics.org/apics-for-business/products-and-services/apics-scc-frameworks/scor (accessed 2017-10).
- 8)PCI SSC: Payment Application Data Security Standard, Version 3.2, https://www.pcisecuritystandards.org/documents/PA-DSS_v3-2.pdf (accessed 2017-10).
- 9)PCI SSC: ATM Security Guidelines, https://www.pcisecuritystandards.org/pdfs/PCI_ATM_Security_Guidelines_Info_Supplement.pdf (accessed 2017-10).
- 10)Common Criteria, https://www.commoncriteriaportal.org (accessed 2017-10).
- 11)Bull-Dat-Diebold-NCR-Siemens-Nixdorf-Wang-Global: Automatic Cash Dispensers/Teller Machines Protection Profile Version 1.0, PP/9907, https://www.commoncriteriaportal.org/files/ppfiles/PP9907.pdf (accessed 2018-6).
- 12)Common Approval Scheme: Point of Interaction Protection Profile Version 2.0, http://www.ssi.gouv.fr/uploads/IMG/certificat/ANSSI-CC-cible_PP-2010-10en.pdf (accessed 2017-10).
- 13)NIST: National Checklist Program Repository, https://web.nvd.nist.gov/view/ncp/repository (accessed 2017-10).
- 14)Microsoft: Security Compliance Manager, https://technet.microsoft.com/en-us/solutionaccelerators/cc835245.aspx (accessed 2017-10).
- 15)CERT: SEI CERT Coding Standards, https://www.securecoding.cert.org/confluence/display/seccode/SEI+CERT+Coding+Standards (accessed 2017-10).
- 16)ISO 31000:2009, Risk management - Principles and guidelines.
- 17)PCI SSC: List of Validated Payment Applications, https://ja.pcisecuritystandards.org/approved_companies_providers/vpa_agreement.php (accessed 2017-10).
- 18)PCI SSC: Approved PIN Transaction Security (PTS) Devices, https://www.pcisecuritystandards.org/approved_companies_providers/approved_pin_transaction_security.php (accessed 2017-10).
- 19)JISEC, Finger Vein Authentication Device UBReader2 Hardware: D, Software: 03-00, http://www.ipa.go.jp/security/jisec/certified_products/c0332/c0332_it1353.html (accessed 2017-10).
- 20)Hitachi: Research & Development, http://www.hitachi.com/rd/ (accessed 2017-10).
- 21)Hitachi: Hitachi Incident Response Team, http://www.hitachi.co.jp/hirt/ (accessed 2017-10).
- 22)ATM Industry Association, https://www.atmia.com/ (accessed 2017-10).
- 23)PCI Security Standards Council, https://www.pcisecuritystandards.org/ (accessed 2017-10).
- 24)Connected Consumer Device Security Council, https://www.ccds.or.jp/ (accessed 2017-10).
Belongs to Hitachi Ltd., Research & Development Group, Center for Technology Innovation-Systems Engineering, Security Research Department. Researches ATM security, cloud security, and security management. A member of IPSJ, JSSM and CISSP. Ph.D.
Tomoyoshi Ishikawa (non-member)Belongs to Hitachi-Omron Terminal Solutions, Corp., Software Development Center. Develops ATM controllers and their security. A member of CEN Workshop on eXtensions for Financial Services. Registered Information Security Specialist (No.006397) and PCI Professional.
Hisao Ogata (non-member)Belongs to Hitachi-Omron Terminal Solutions, Corp., Products and Maintenance Services Strategy Division Global Business Group. Constructs overseas business strategies. A member of IEICE and ISO/IEC JTC1 SC37.
Takumi Sanada (non-member)Belongs to Hitachi-Omron Terminal Solutions, Corp., Software Development Center. The work is managing ATM development.
Accepted:March 30, 2018
Editor:Atsuhiro Goto (Institute of Information Security)